WorkShop n°11 : Monitoring (and interfering) an SSL communication
In this workshop, we are going to demonstrate how an existing secured client-server HTTPS communication (HTTP over SSL) can be monitored and debugged very simply with TcpCatcher.
In order to achieve this, TcpCatcher has a unique capability : it can behave like an SSL Server in between the client and the target server. This SSL server can be using a single static X509 certificate or runtime generated certificates in order to make it fully transparent for the client application (often called "man in the middle" technique).
- For demonstration purposes, we are going to monitor our secured communication between our browser and gmail (https://mail.google.com)
- Start TcpCatcher and make sure your browser is configured to use TcpCatcher as a web proxy on port 8200 here (that is automatic for Internet Explorer users)
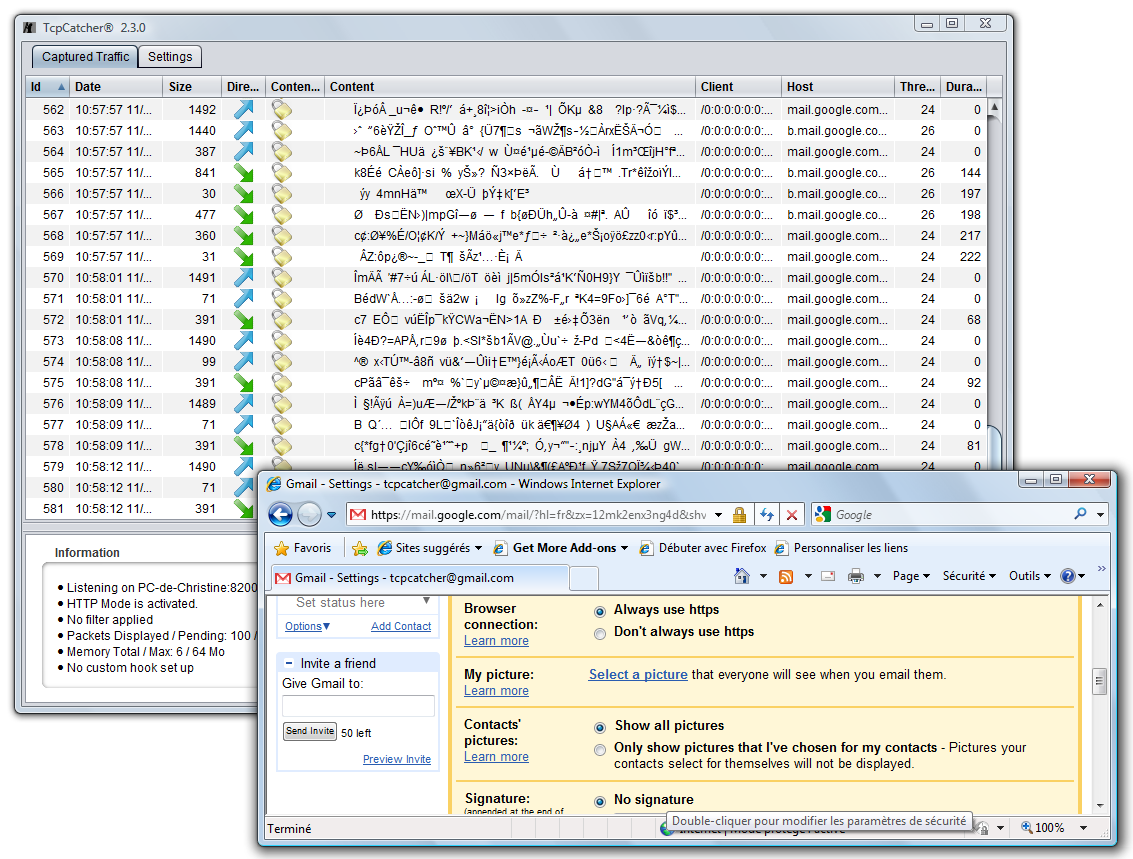
- If we keep defaults TcpCatcher settings (option 'Tunnel SSL'), TcpCatcher behaves like a regular web proxy and SSL data is simply tunneled through the proxy ; we don't see much but an encrypted stream of octets... Notice the padlock icons for SSL packets..
- Now, let's check the 'Monitor SSL' option, and first in order to understand what we're going to do after, we are going to choose the 'static certificate' option (and we are going to open an SSL server on any availabe port, for example 8201 ; but your client is not going to access this port directly)
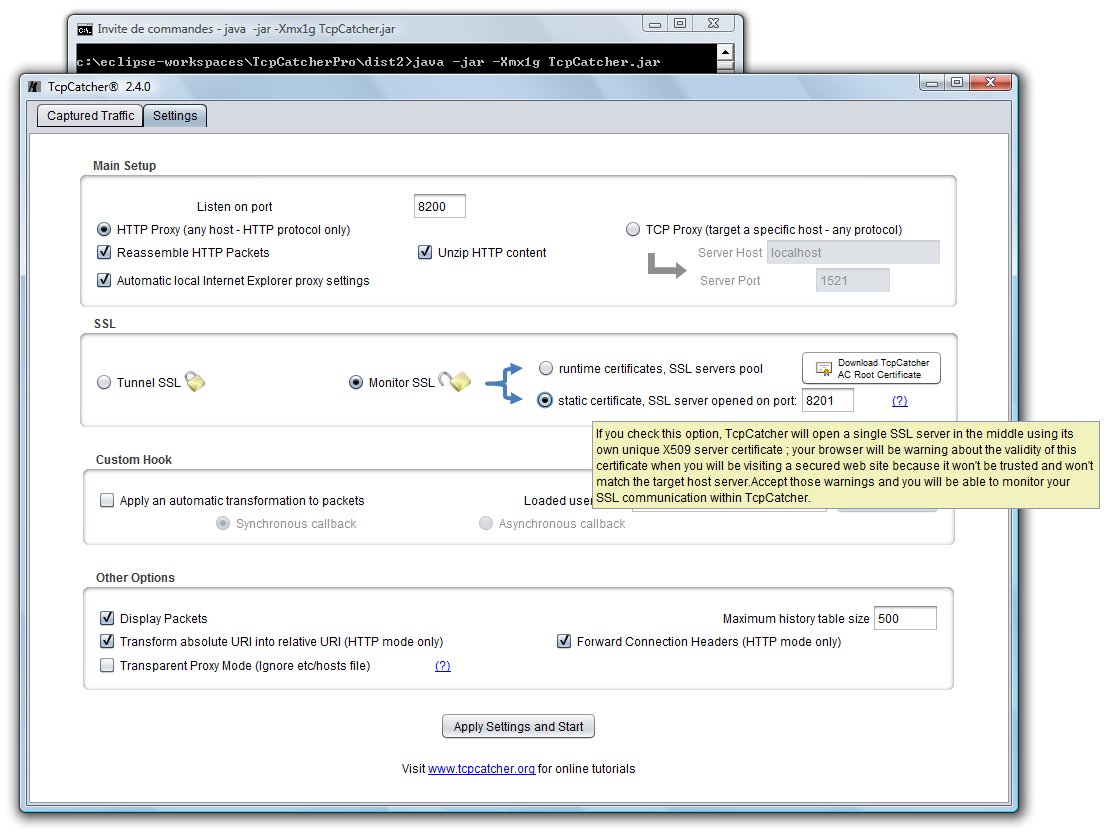
- Click 'Apply Settings and Start' and visit https://mail.google.com with your favorite browser .
Now, your browser will be be warning you about the certificate for two reasons :
- it is not trusted by a known Certification Authority (it is self signed)
- it does not match the site we are visiting (mail.google.com)
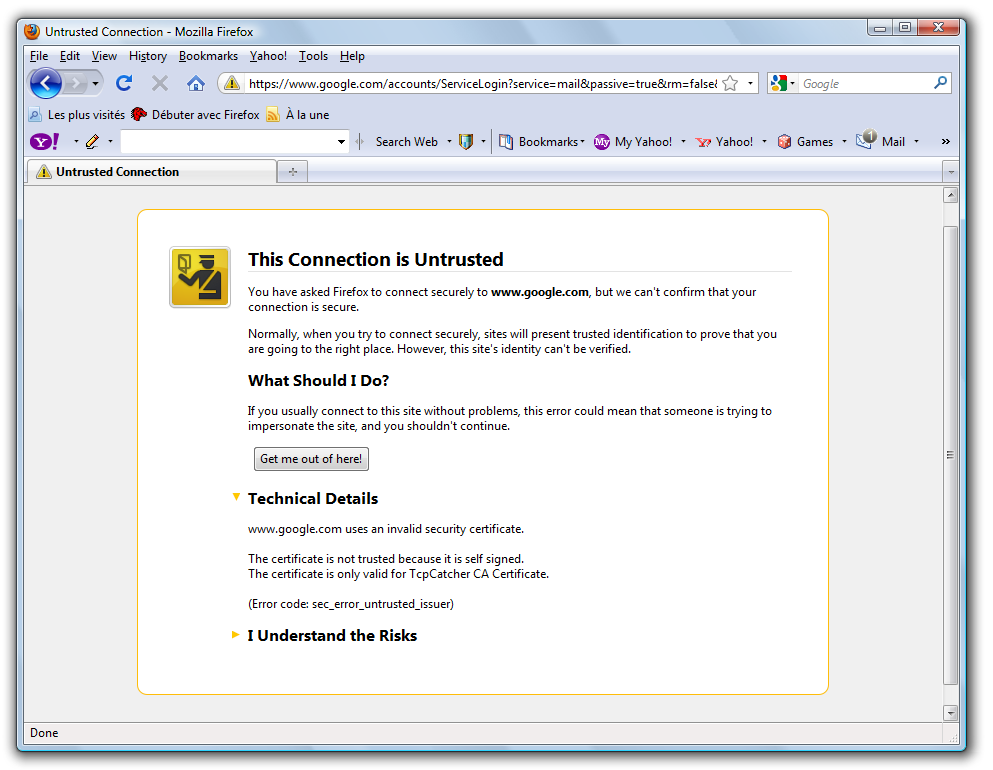
That is logical, because your browser is not receiving Google's cerficate but TcpCatcher's static one.
Let's accept these security warnings and continue ('I understand the risk and add security exception..').
And now we are monitoring our HTTPS conversation ! Notice the opened padlock icons for decrypted SSL packets..
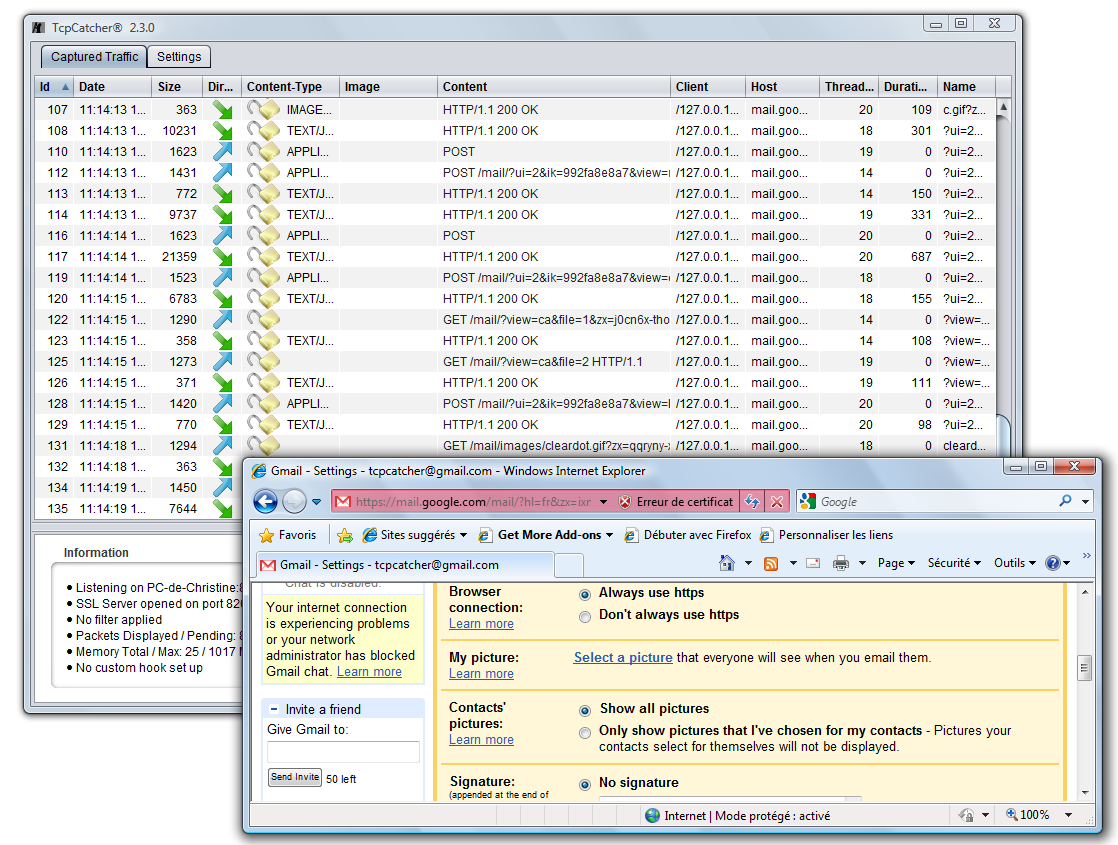
- Now let's try the option 'runtime certificates' in order to make it fully transparent for our browser.
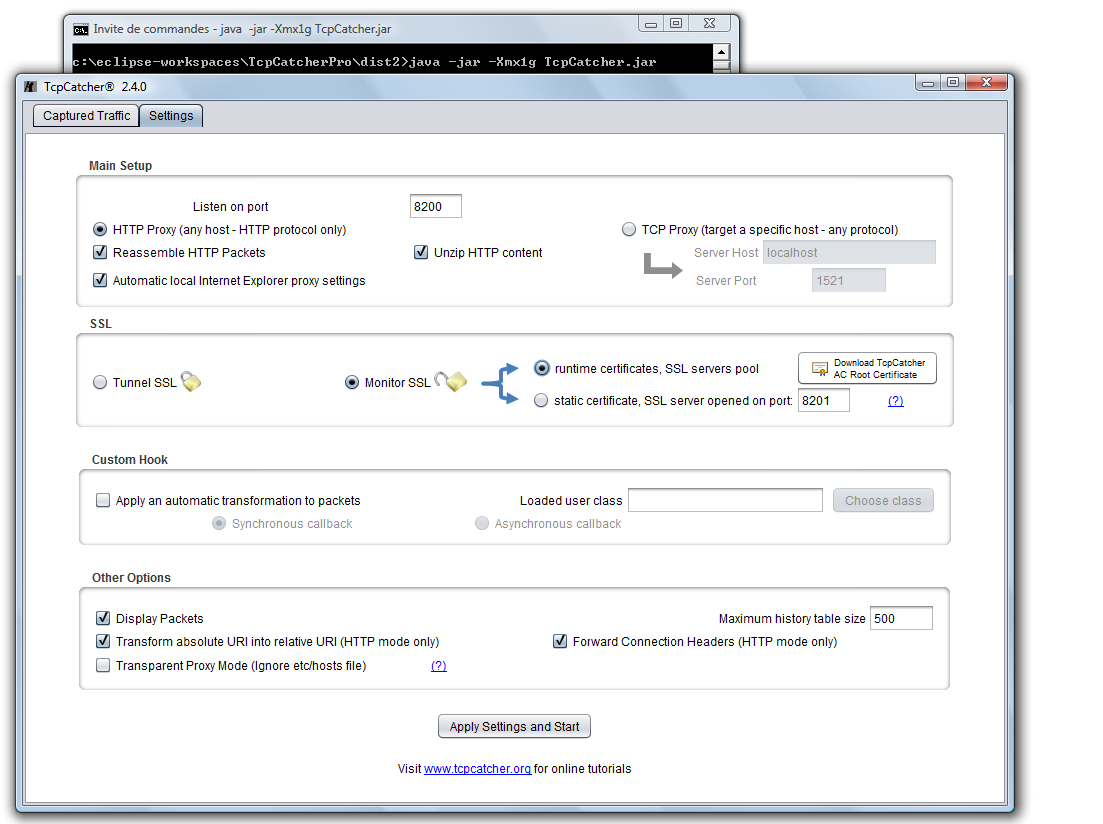
If we choose this mode, TcpCatcher is going to generate X509 certifcates on the fly matching requested target hosts server so we are going to get rid of the first issue (certificate not matching web site).
At this point, there is still another issue, your client is not trusting TcpCatcher's certificates. Since TcpCatcher signs all its runtime generated certificate with its own AC root certificate, you only need to add once for all the TcpCatcher Root Certificate into your trusted list.
First click on the 'Download AC Root Certificate' to download the .cer file also available here.
Then, let's import into our browser this root certificate (of course you can remove it from your truststore whenever you wish).
With Firefox: Tools | Options | Advanced | Encryption | View Certificates | Authorities | Import.. then browse to your downloaded TcpCatcher-ACRoot-Certificate.cer file.
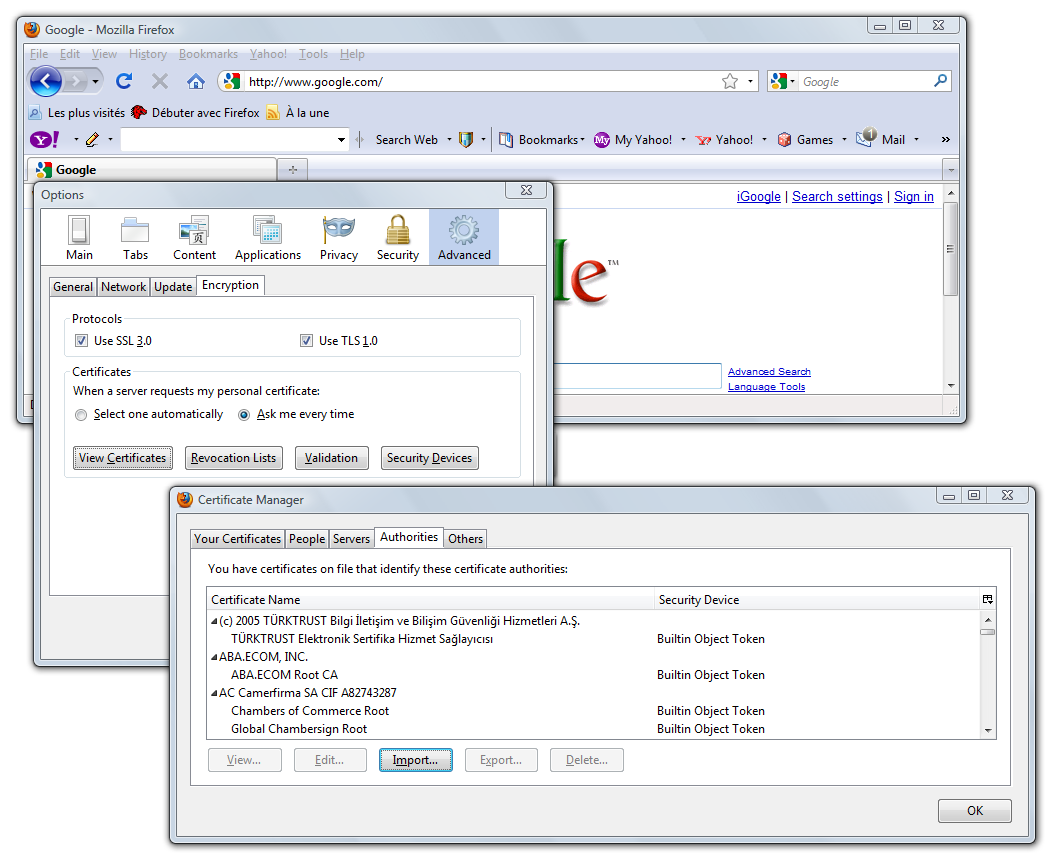
then check 'Trust this CA to identify web sites'
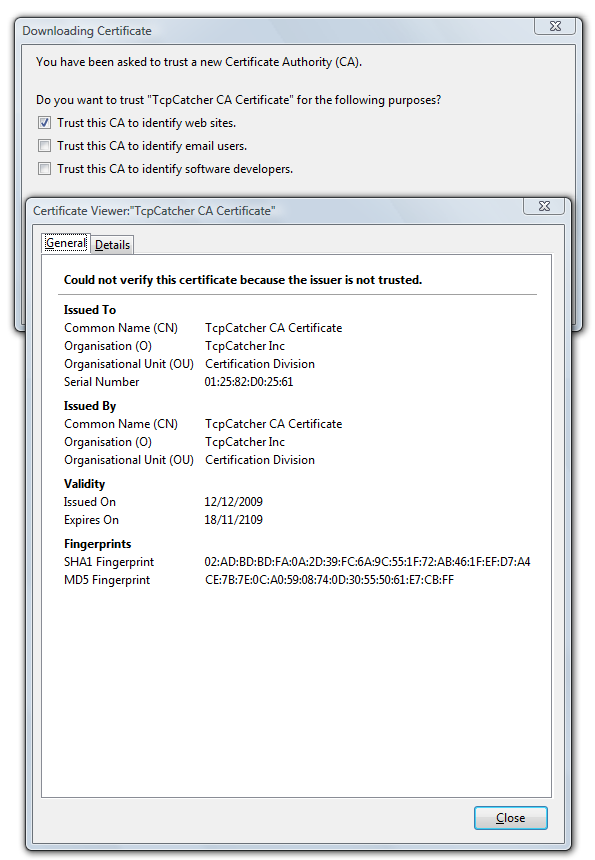
Now we can monitor and interfere once for all any secured web site visited without any warnings at client level !
- You can watch the screencast describing that on Windows and with Internet Explorer (it is even faster)








