In some situation, you may want to use TcpCatcher to monitor and debug a none HTTP communication that is secured with SSL. This can be LDAPS, POPS, .. any protocol over TCP/IP between a client and a server.
For demonstration purposes, let's see how to monitor the communication between our Outlook desktop client and our remote IMAP mail server at Google's. The communication is secured with SSL but TcpCatcher will be our man in the middle.
- First let's start TcpCatcher, check the option 'TCP Proxy' (because we are not dealing with an HTTP communication)
- Enter target endpoint to redirect traffic: target server is "pop.gmail.com" and target port is 993 and check the option "Monitor SSL communication"
- Notice that this last option will instruct TcpCatcher to open its own SSL server on port 993 using a forged certificate using the name ""pop.gmail.com" (this certificate is signed using the TcpCatcher AC Root).
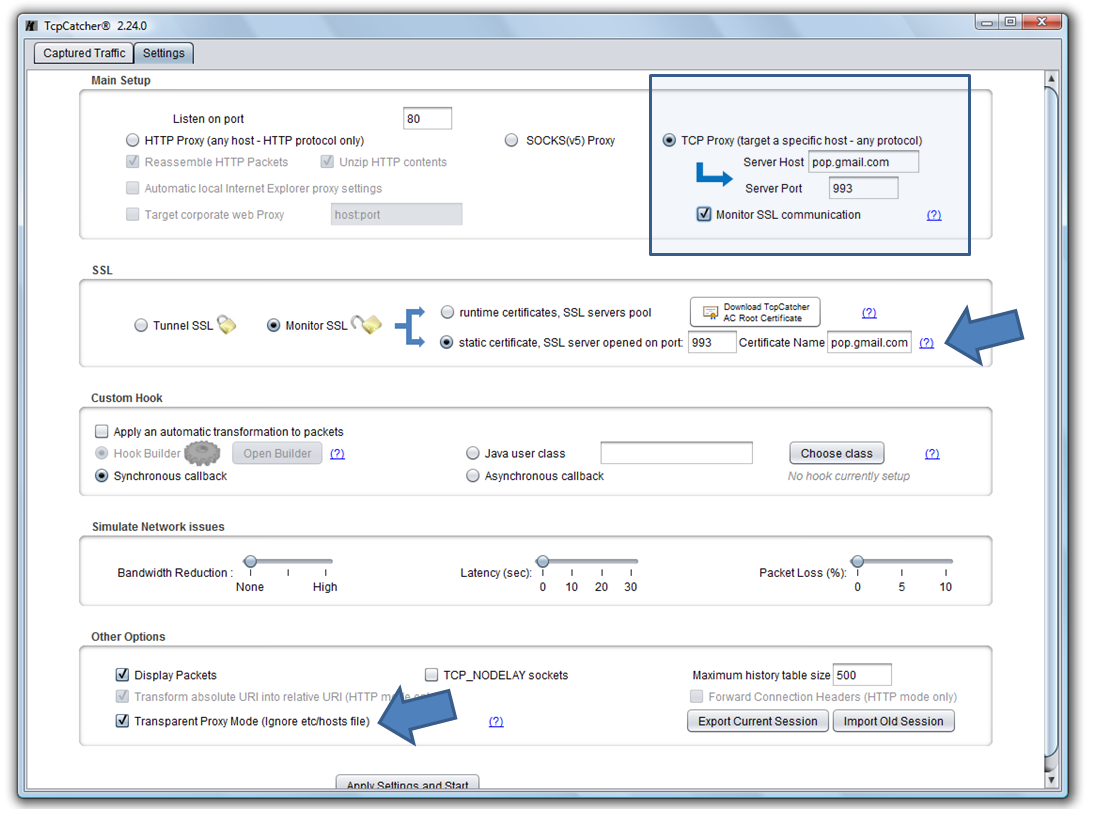
- Notice also that the option 'Transparent Proxy Mode' has been checked. Outlook is not going to be aware that there is a proxy in the middle.No modification is required at Outlook configuration level, but we need to add an entry in our etc\hosts file to map pop.gmail.com to our localhost (assuming TcpCatcher is running on local host) so TcpCatcher will receive all the requests targeting pop.gmail.com. Because we have checked the 'Transparent Proxy' option, TcpCatcher will ignore this network redirection and will still resolve the actual gmail ip.
C:\Windows\System32\drivers\etc\hosts file or for Linux users /etc/hosts file
- Now , let's press "Apply settings and start" and our secured IMAP communication is captured in plain text :




